A new wave of Nymaim malware stands out for efforts to disguise its appearance – and not for delivering an original payload. Nymaim is an old-school Trojan spread by spear phishing. It has been used to distribute a number of threats to the end user’s computers such as ransomware, data-stealing malware, and exploit kits. Active since at least 2013, it is a well-known and well-recognized bit of malware. And that is what makes its latest transition so interesting.
Knock, knock, it’s (not) Nymaim
Malware such as Nymaim works like a door-to-door salesman: It knocks, presents itself as selling anything from brushes to ice cream, then once in the door, gets busy with the fraudulent activity.
From the antivirus perspective, the real challenge is spotting Nymaim when it first knocks and presents itself to the targeted computer. Once Nymaim can unpack its bags and get to work – it’s really too late from the preventive security angle. This is why an early unwinding of the new obfuscation is so important.
Obfuscation by the book
Obfuscation is to make something less clear and harder to understand. The word is often used to describe politicians, lawyers, and malware developers. The latter use an array of obfuscation techniques to protect malicious code from detection and also slow down the analysis process for the antivirus program.
No obfuscation for dummies
“What’s new now is the new level of obfuscation Nymaim is using to protect its binary,” said Shahab Hamzeloofard, malware analyst at Avira. Nymaim is using both code flow and stack code obfuscation.
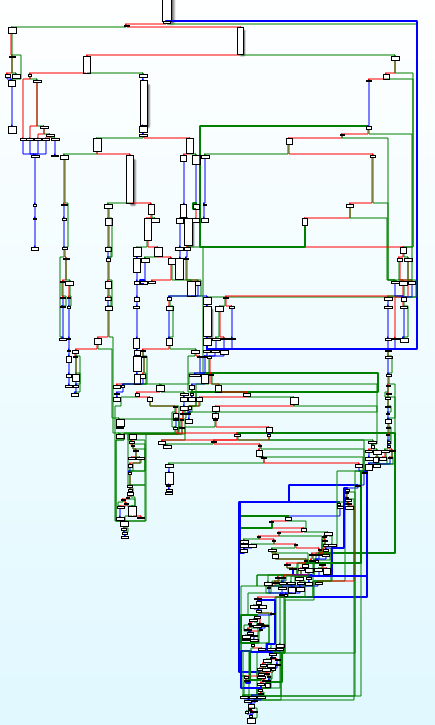
The level of obfuscation is clearly visible in the code flow graphs of one of Nymaim functions – before and after deobfuscation. “It uses lots of dummy comparisons with conditional jumps to obfuscate the code flow,” he explained. “If you compare this graph and the deobfuscated graph, you can see Nymaim is heavily obfuscated. In the first graph, we have more than 200 code blocks, after deobfuscation in the next graph you can see it’s just 8 blocks.”
Well-stacked malware
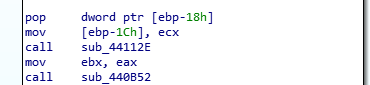
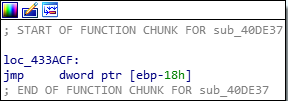
Nymaim also has some functions that are started with a very strange set of instruction without allocating stack frame and which use the caller stack frame. “Below we can see how it gets the return address via pop instruction and at the end jumps to the return address. We use IDA script to do notation for stack variables to make code readable,” said Shahab.
Fight to be continued …
Obfuscation is an important element in the cat-and-mouse fight between malware developers and security analysts. The bad guys need it to disguise themselves so they can work their way into the targeted device. Antivirus developers must constantly hone their deobfuscation skills as shown by Shahab to increase the antivirus effectiveness.