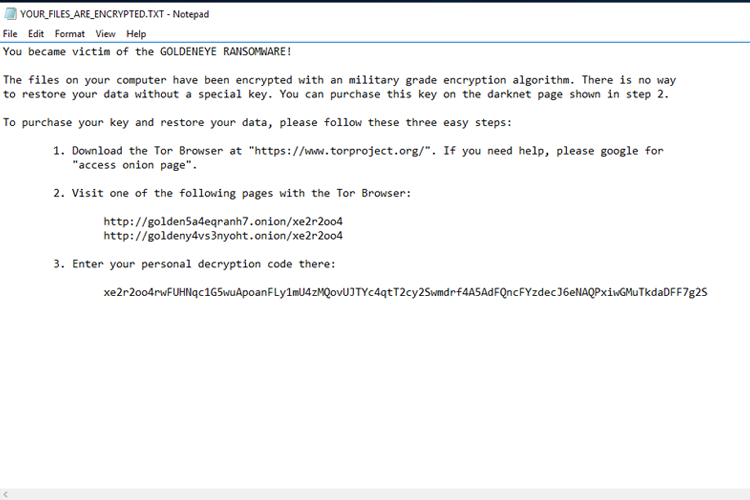
Cybercriminals usually use Pop culture to choose ransomware names: there is one related to Pokémon, Mr. Robot, and many more. This time it seems to be related to the 1995 James Bond movie or the device that appears in it: an electromagnetic Soviet satellite weapon from the Cold War. It looks like the similarities end with the chosen name though.
The ransomware has first been discovered in Germany trying to spread via a fake job application mail. This mail comes with an attached excel file that uses the Macro vulnerability to get on to the system. Once it’s opened and the macro enabled, all hope is gone: the infection process has started.
This excel file will execute two other .exe files that will take care of starting the infections. In the sample we examined, a .txt file with the following text was deposited on the desktop:
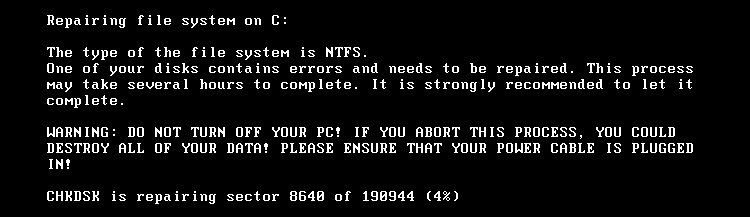
Now, if you read fast enough you will be able to see that you were infected by ransomware. There won’t be any time to get angry about it though, because the system will crash:
It seems like the ransomware we got uses more than one encryption method, as the .txt message and the infection type don’t really go together. The .txt talks about file encryption but what we got here is different: instead of encrypting files it denies access to the whole system. The MBR (master boot record) of the system is being overwritten with their own boot loader, which will go to a custom kernel after a system crash and reboot. This kernel will continue encrypting the system while it makes you believe that it is being repaired instead.
Now, after the job’s done it will tell you that the full disk is encrypted but it encrypts the MFT (master file table) which makes it impossible for us to read the system. Wait – we’ve seen something like that before in job applications! The malware is called Petya and not Goldenye, the rest is exactly the same though.
Related article
https://blog.avira.com/petya-hr-engineering/
Even if it calls itself Goldeneye Ransomware, the behavior is exactly the same as Petya. They even display the same message as before with only changing “files” to “harddisks”.
You never know how this malware will creep up on you. The cybercriminals rely on social engineering tricks to fool more users into opening their files and are very creative with it (this time it was a job application). So always be vigilant. Think twice before opening any mail attachment or link. If you have the smallest suspicion that it might be any kind of malware, get rid of the mail.
Anyway, we already detect these new malware files for you, so you can feel more secure!