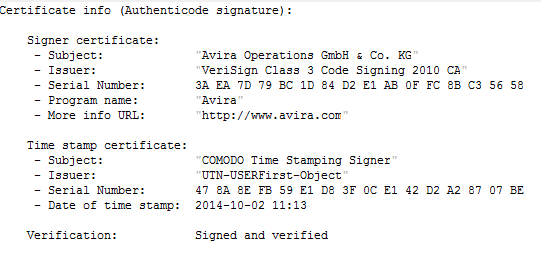
Digital Certificates contain some or all of the following information (not all of these attributes have to be specified):
- Program Name: Name of the software.
- Publisher Link: Link to the software developer / company.
- More Info Link: Additional link to a specified area.
- Signer Serial Number: Contains the serial number of the signer (in Hex-Code).
- Signer Issuer Name: Name of the signer who certificated the software.
- Signer Subject Name: Name of the company which created the software.
- Timestamp Serial Number: Timestamp when the serial number was created (in Hex-Code).
- Timestamp Issuer Name: Company name of the signer with the specific timestamp of certification.
- Timestamp Subject Name: Company name of the signer with an additional timestamp.
- Date: Date when the software was created.
This is what a certificate looks like in a debugger view:
Below you can see the same certificate as before but in the general MS Windows overview.
Things are changing though: Since malware authors have found ways to steal or fake digital certificates, one can never be really sure if a file with a valid certificate is legit or not.
Suspicion: How can I find out if a digital certificate is trustworthy?
- First of all, the certificate should be valid and not expired. Anything else could be seen as suspicious, although not reliably so, for example an old tool might indeed have an expired but actually valid certificate.
- Another very easy way would be to compare if the software which was e.g. downloaded has the same name as declared in its signature. If that’s not the case, it is possible that the certificate was stolen or faked.
- It is also always good to see if the certificate contains a countersignature. In some cases, it could be a sign for malware if this information is missing.
- An additional quick web search often brings more information about the reputation and trust-level of a certificate issuer or their software.
Also, it is necessary to know if a signature is still valid or expired. This might bring additional value to the classification, although when working with adware, one often encounters valid signatures.
The other way around: Classifying files based on digital certificates
On the other hand, adware vendors also use certificates to make sure their files are theirs. We, as an Antivirus company, can use this to our advantage. It enables us to classify files being suspicious of Adware or other possibly unwanted applications in a very simple manner.
If it is known that a certain adware type is always certified by the same certificate issuer, we can classify this issuer as potentially adware-related. Any new unknown file that is also signed by this issuer, now also is considered to be potentially adware-related. This works for all other prefixes as well, like APPL, PUA etc.
Obviously, this way of classification is not highly secure, but it gives us the opportunity to quickly find and easily filter certain amounts of files for further analysis and creating detections.
Let’s take a look at an example:
This is a valid certificate of a known adware vendor of the PUA/InstallCore family. Starting here, we can gather that most of the files which have “Digital Digest Pty Ltd” as the certificate issuer are part of the same adware family. A simple google search confirms it and verifies the fact that said issuer is at least suspicious to a certain amount.
Several departments within the Avira Protection Lab (e.g. the engine team and protection QA) act as additional sources for suspicious certificate names. Anyone who processes a lot of files and sees any similarities in the certificates is providing the virus lab with the information needed to make a classification. This cross-department communication has proven very useful in the past and has led to many synergy effects.
Back on topic, the same vendor could use different names for the signatures.
Conclusion
Certificates are very powerful as an analysis instrument. They cannot and will not replace conventional detection creation though; being simple ASCII-Text based makes them not 100% reliable. But as a quick and easy addition they serve their purpose well.
This post is also available in: German